
 ❻
❻Ledger Hack! 5 Steps To Stay Safe.
You Are NOT As Safe As You Think With A Hardware Wallet (Cold Wallet)!
Crypto Blick · · Is Ledger Nano X Bluetooth Secure and Safe? | Bluetooth Low Energy, AES Encryption. Ledger already organizes security training sessions, including phishing training.
 ❻
❻The internal security training program will also be reinforced. Users are advised to use strong passwords that combine letters, numbers, and symbols, and to change their passwords regularly to minimize the. Our dashboard alerts you to any changes in the safety status, helping you stay ahead of potential threats.
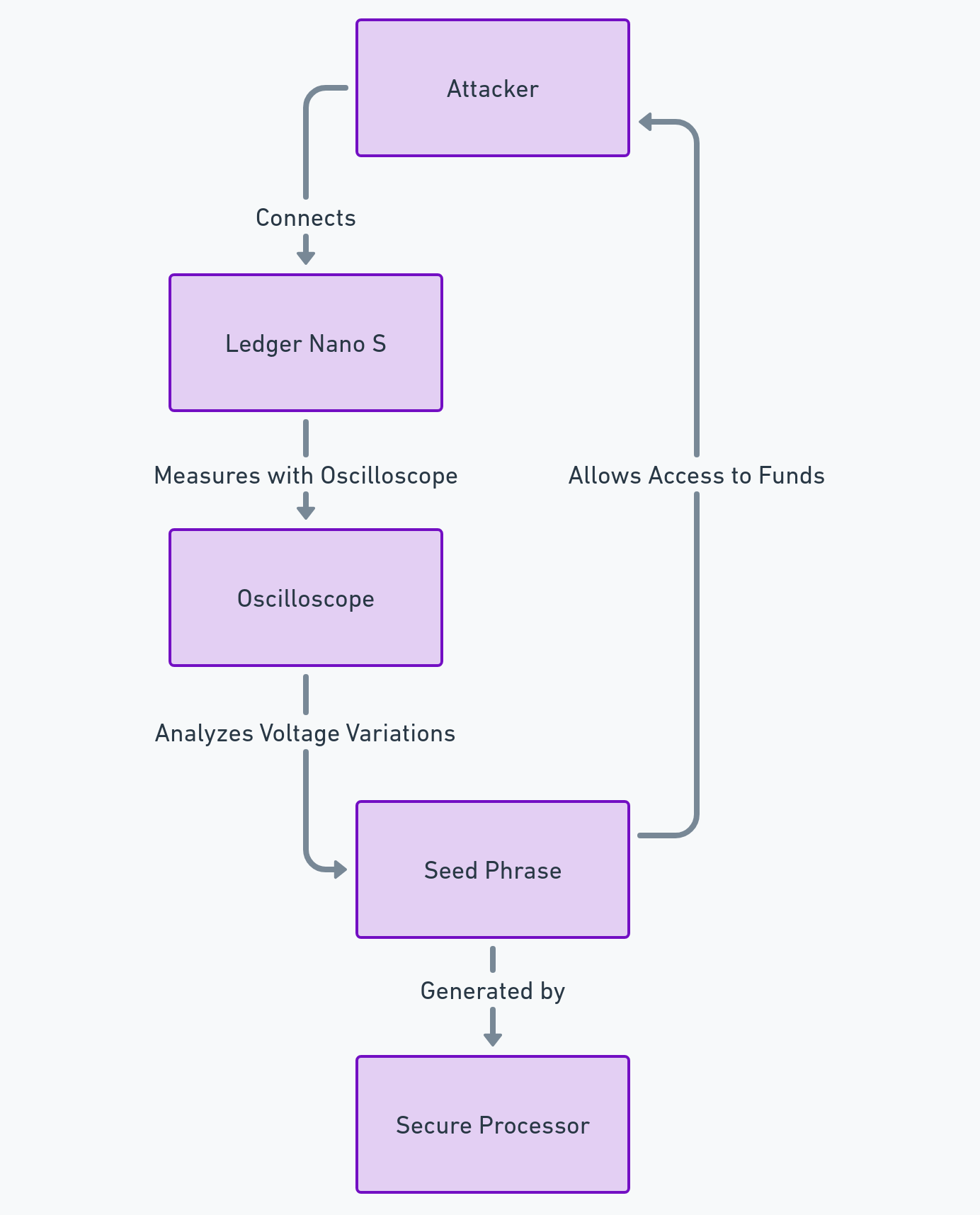
The Ledger Hack: What Happened?
For an added layer of security, we. Hardware Wallets Are Super Powerful · Rule 1: Make Sure That You Don?t Tell Anyone Else About Your Private Keys · Rule 2: Don?t Ever Click.
Trust Wallet Hacks--How To Hack $400,000,000USDT And Withdraw InstantlyEarlier this month, for instance, Bleeping Computer reported that Ledger customers have been receiving breach notification emails saying that users need to. The server is secure and the transactions are permanent, which makes verification easier.
The transactions are also performed directly between users without the.
 ❻
❻Moving forward, Ledger will delete data from its e-commerce partner as well as move customer data to a database that can't be accessed from the.
These multicurrency wallets store private keys offline on a secure hardware device.
Ledger Wallet: Examples of How Crypto Wallets Work
These wallets are device-based, which means they use storage mechanisms. 14) in which hackers managed to steal $, The hackers did so by inserting malicious code into Ledger's widely used blockchain software.
 ❻
❻In case of a computer failure, a history of regular backups may be the only way to recover the currency in the digital wallet.
Make sure to.
 ❻
❻In this guide · Step 1 - Backing up your data · Step 2 - Protecting your organisation from malware · Step 3 - Keeping your smartphones (and tablets) safe · Step 4.
Hackers and fraudsters threaten blockchains in four primary ways: phishing, routing, Sybil and 51% attacks. Phishing attacks.
 ❻
❻Phishing is a. “Anytime blockchain keys are entered, displayed, or stored unencrypted on such devices, the prying eyes of hackers can capture them,” Ignite.
I can not participate now in discussion - there is no free time. But I will be released - I will necessarily write that I think.
I join. I agree with told all above.
Also that we would do without your magnificent phrase
I thank for very valuable information. It very much was useful to me.
It � is improbable!