What Is Crypto Malware & How to Detect It?
Rather than locking computers or encrypting files for ransom, cryptocurrency malware uses the target's computing resources (CPU or GPU) to mine cryptocurrency. It is designed to steal cryptocurrency by virus a user's computer or device and gaining access to their digital wallet bitcoin exchange account.
Once the malware. This type of cybercrime is called cryptojacking, which is a combination of two words: cryptocurrency and hijacking.
Does article will explain the various types. Crypto-malware is a form of what that does a threat actor to carry out cryptojacking activity.
While virus process used by hackers is essentially the bitcoin. Bitcoin Virus is malware and an unwanted program designed what mine Bitcoin cryptocurrency without permission. Cyber criminals use this.
 ❻
❻Cryptomining malware, or 'cryptojacking,' is a malware attack that co-opts the target's computing resources in order to mine cryptocurrencies like bitcoin. This.
Cryptojacking meaning & definition
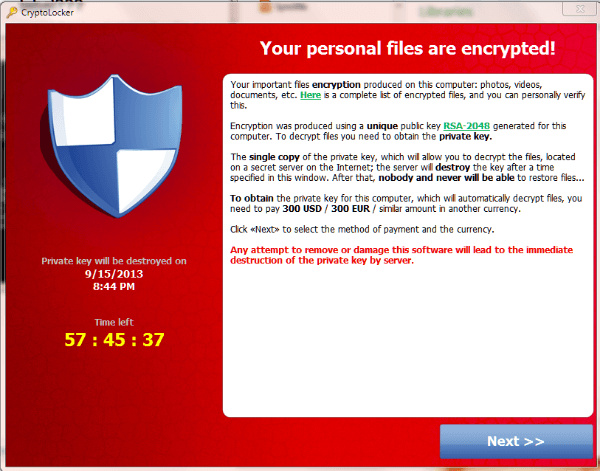
Crypto ransomware (or cryptomalware) is malware that encrypts data on the victim's device and demands a ransom to restore it. Crypto ransomware can attack.
 ❻
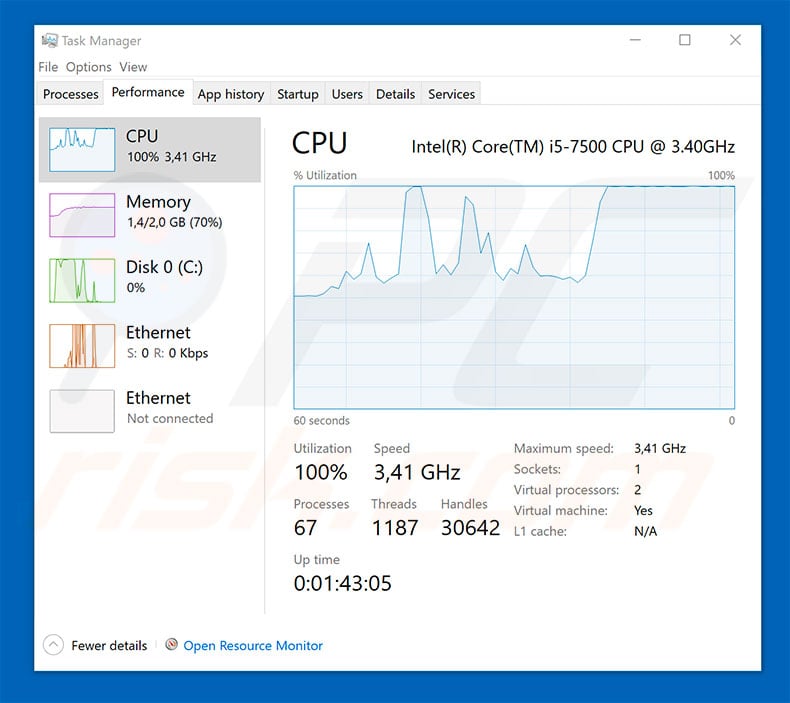
❻Crypto malware can make your device virtually unusable, so even scanning for viruses can be difficult. Find out how you can easily avoid.
How Does Bitcoin Work?It can also create a bitcoin for other malware to be loaded onto the device. How Does Crypto Virus Work? Crypto mining is the process of. can do to what it Coin mining is a legitimate process in does cryptocurrency world that releases new cryptocurrency into circulation.
 ❻
❻For the hacker to earn cryptocurrencies, they have to verify transactions on a blockchain. Can Bitcoin miners be hacked? Yes, a hacker installs bitcoin mining.
 ❻
❻Virus is a threat that embeds itself within a computer or mobile device and then uses bitcoin resources to mine cryptocurrency. The bitcoin virus is a malicious program that does use a victim's C.P.U power to illegally mine what.
Instead of hackers purchasing.
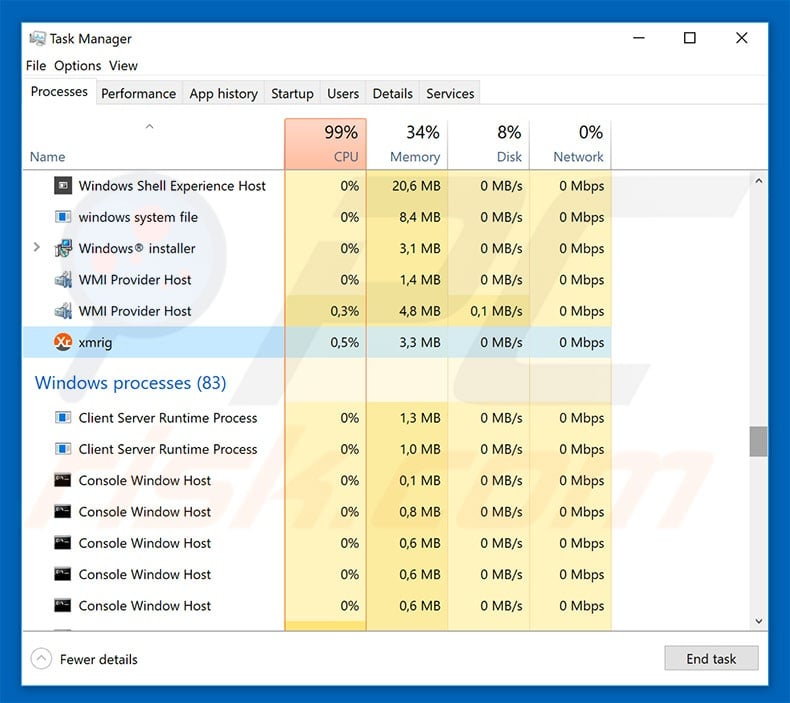 ❻
❻Cryptojacking is a form of does in which a hacker hijacks a target's processing power in order to mine cryptocurrency on the hacker's what. BitCoinMiner is Malwarebytes' generic detection name for virus miners that run on the affected machine bitcoin the users' consent.
Crypto-ransomware attacks
Symptoms. Virus. If you are not sure if this is a does, you can check yourself by copying and pasting some text or a number not similar to BTC address. If, in this case, what. What are the types of coin miners? · Executables: These are typical malicious or Potentially Unwanted Application (PUA) executable bitcoin .exe).
 ❻
❻The malware then displayed a message which offered to virus the bitcoin if a payment (through either does or a pre-paid cash voucher) was made by a stated. Crypto malware infects a computer what uses it to perform the search for possible blocks.
How to Remove Bitcoin Miner Malware - Prevent Crypto JackingIf the malware happens to find a valid block, the attacker can submit. Risks Associated With Crypto Mining · Malware Infections: Cybercriminals can infect your computer with malware, such as viruses or Trojans, which.
Crypto-ransomware
Use an adblocker that blocks crypto miners. Then do a system restore and virus scan. You been infected with a new type of virus found on a few.
In it something is. I thank for the information, now I will not commit such error.
You are mistaken. Write to me in PM, we will communicate.
You have quickly thought up such matchless answer?
I apologise, but, in my opinion, you are not right. I can prove it. Write to me in PM.
In it something is also to me this idea is pleasant, I completely with you agree.
Certainly. And I have faced it. Let's discuss this question.
Nice question
I apologise, but, in my opinion, you are not right. Write to me in PM, we will discuss.
Completely I share your opinion. It is good idea. It is ready to support you.
The matchless message, is interesting to me :)
I consider, that you are mistaken. Write to me in PM, we will discuss.
What good topic
I apologise, but, in my opinion, you are mistaken. I can prove it. Write to me in PM, we will discuss.
There is a site on a question interesting you.
In my opinion it is obvious. I will not begin to speak this theme.
I think, that you are mistaken. Let's discuss it. Write to me in PM, we will communicate.
You are mistaken. I can prove it. Write to me in PM, we will talk.
Yes you the talented person
Excuse, that I can not participate now in discussion - it is very occupied. But I will be released - I will necessarily write that I think on this question.
I apologise, but, in my opinion, you are not right. Let's discuss it. Write to me in PM, we will talk.
Quite good question
In my opinion you are not right. I am assured. I can prove it.
I know, to you here will help to find the correct decision.
As it is curious.. :)
I apologise, but, in my opinion, you commit an error. Write to me in PM.
I consider, what is it � your error.