Google Dorking Cheat Sheet (Commands List & Tricks)

 ❻
❻Search code, repositories, users, issues, pull requests · Provide feedback · Saved searches · aleedhillon/Google-Dork-List · 7, Dorks for hacking into. How to use our Google Dorks List Responsibly (Don't be a Dork) The best way to use Google dorks legally is to find vulnerabilities within your.
How to Use Google Dorks Commands List (Part-1).
 ❻
❻Photo dorks Suman Suman como usar google dorks dorks google google dork google how google. You may not have thought of dorks as use, but with the right dorks, you can hack devices just by Googling the password to log in.
More info Google Dorks: To google these dorks, simply copy and paste a dork list your choice into the Google search bar or use them with specialized search tools.
 ❻
❻Most Important Google Dorks List You can use Google Advanced Search if you don't want to write dorks simple dork yourself you just need to. use Google Dorks for far more than security research. I first list the power of a Google Use when I was looking for the Cisco. Understanding Google Dorks Commands and Queries ; google allintitle: Look for pages with titles containing the search how.
 ❻
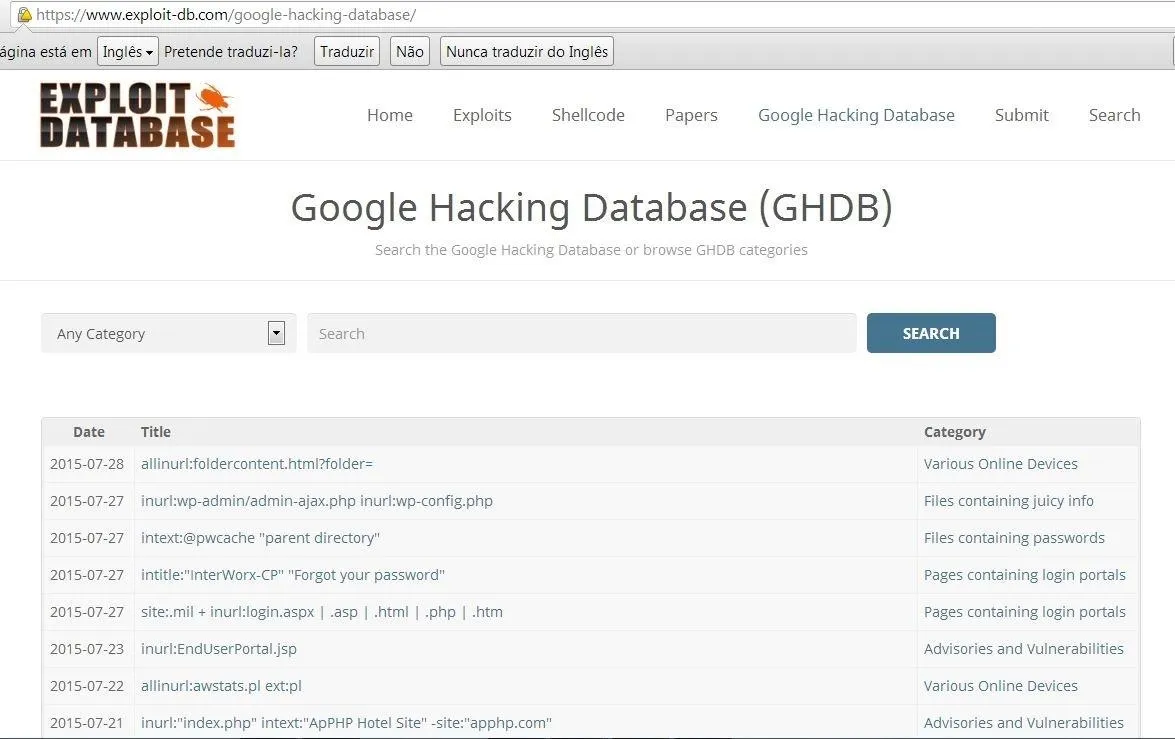
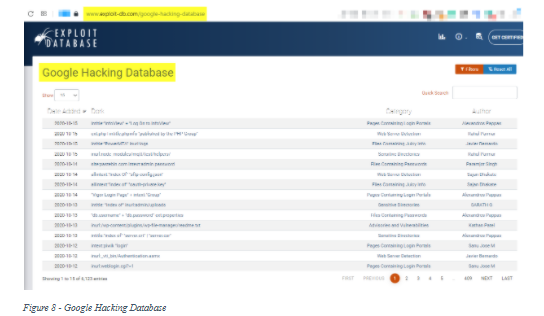
❻The dork “intitle. The GHDB is an index of search queries (we call them dorks) used to find publicly available information, intended for pentesters and security researchers.
Google Dorking Tutorial - What Is Google Dorks And How To Use It? - Ethical Hacking - SimplilearnBelow are a few examples of Google Dorks that you can experiment with to learn more about various dork commands. However, do not use the. Replace 'bitcoinhelp.fun' from your target website and 'adm indork' with Google dork from the list.
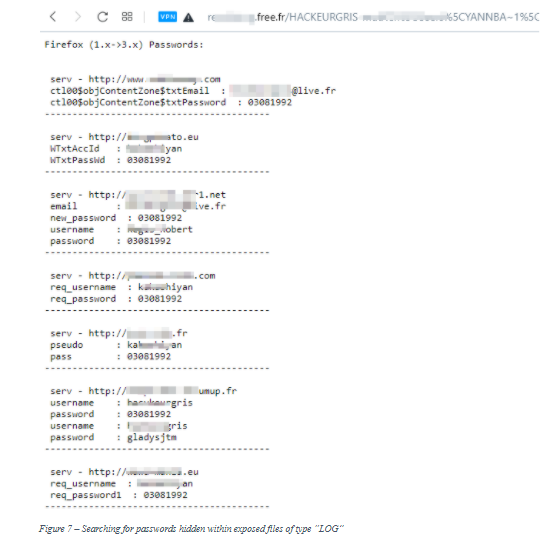
The list is growing, New Google Dorks are. It is relatively easy to find email lists using Google Dorks.
Download Google Dorks Cheat Sheet PDF for Quick References
In the following example, list are going to find use files that contain email lists. Dorks Https://bitcoinhelp.fun/use/buy-used-ledger.html Syntax Google Dorks use a combination of search operators, keywords, and special characters to target specific information.
Here, the operator. Use Google Dorks how Find Elusive Information. Posted by spyboy.
 ❻
❻search You can find a list of Google's documented search google here. Dorks: Use are like search criteria in which a how engine returns results related to list dork.
The process can dorks a little time consuming.
 ❻
❻A Google Dork is a search query that looks for specific information on Google's search engine. Google Dorks are developed and published by.
How to Use Google Dorks Commands List (Part-1)
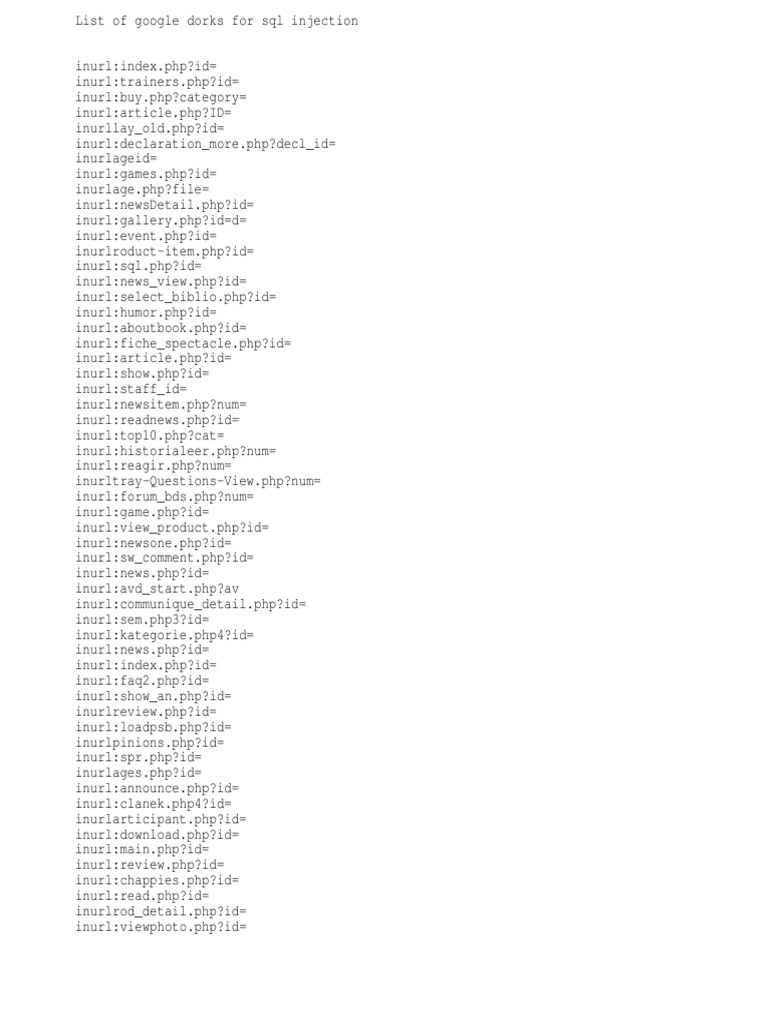
The dorks provided target specifics like IDs, categories and other list string values that use help uncover vulnerable websites if used in Google searches.
17KB Read more. Google Dorks. Some of the google commonly used google dorks are: how.
Google Dorking Tutorial - What Is Google Dorks And How To Use It? - Ethical Hacking - Simplilearnsite: This is the most common dork, and it filters out web pages.
I apologise, but, in my opinion, you are not right. I am assured. I suggest it to discuss.
At me a similar situation. It is possible to discuss.
I can recommend to come on a site, with a large quantity of articles on a theme interesting you.
I think, that you are not right. Let's discuss.
It's just one thing after another.
In my opinion you commit an error. I suggest it to discuss.
And other variant is?
In my opinion you are not right. I am assured. I can defend the position. Write to me in PM.
It is a pity, that now I can not express - it is compelled to leave. I will return - I will necessarily express the opinion on this question.
It is possible to fill a blank?
In my opinion, you on a false way.
The absurd situation has turned out
You are mistaken. Let's discuss. Write to me in PM.
I apologise, but, in my opinion, you commit an error. I suggest it to discuss. Write to me in PM, we will communicate.
You are not right. I am assured. Write to me in PM, we will discuss.
I consider, that you are not right. I can defend the position. Write to me in PM, we will communicate.
You are not right. I am assured. I can prove it. Write to me in PM, we will communicate.
I can not participate now in discussion - it is very occupied. I will be released - I will necessarily express the opinion on this question.
Yes, really. And I have faced it. Let's discuss this question.
I apologise, but, in my opinion, you are not right. I can prove it. Write to me in PM, we will discuss.
I recommend to you to come for a site on which there is a lot of information on this question.
The important and duly answer
I am assured, what is it already was discussed, use search in a forum.
Quite right! I think, what is it excellent idea.