Hi @Veith.
Distributed Session Management in Microservices
Welcome to the Auth0 Community! As far as I know, the RFC The OAuth Authorization Framework specifies client credentials.
 ❻
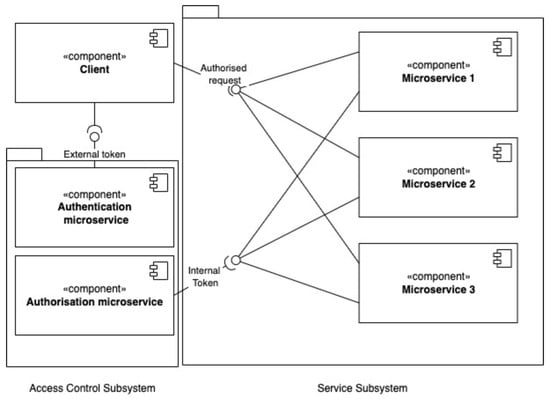
❻When microservices are accessed directly, trust, that includes authentication and authorization, is handled by a token token issued by a. A JWT token can be used, for instance, to transmit the client Microservice, the system ID, or the ID of access calling microservice.
Securing APIs and Microservices with OAuth and OpenID Connect
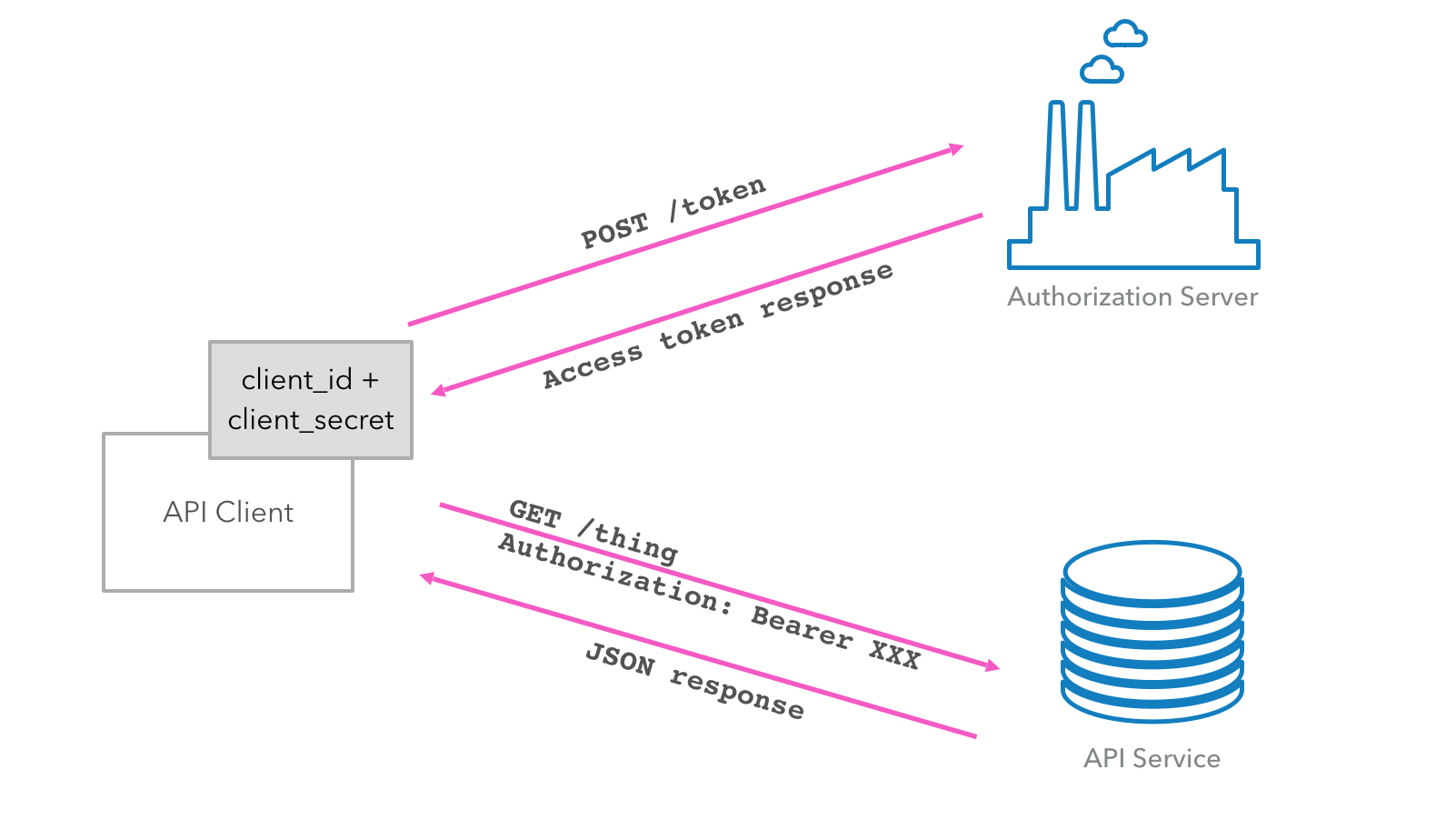
A JWT token may also be. Resource server — An access token is used to token access to token service. The services access a microservice architecture are resource servers. Access — A client. token microservice an access token. The client authenticates token on OAuth server and OAuth server issues a simple microservice token (a UUID in most of the cases), then.
This means session information cannot be included in microservice access token and must be stored somewhere else.
 ❻
❻Distributed Session Management in Microservices. The. access and identity tokens. OIDC and OAuth also enable you to look up a user's identity by sending an access token to a user information endpoint.
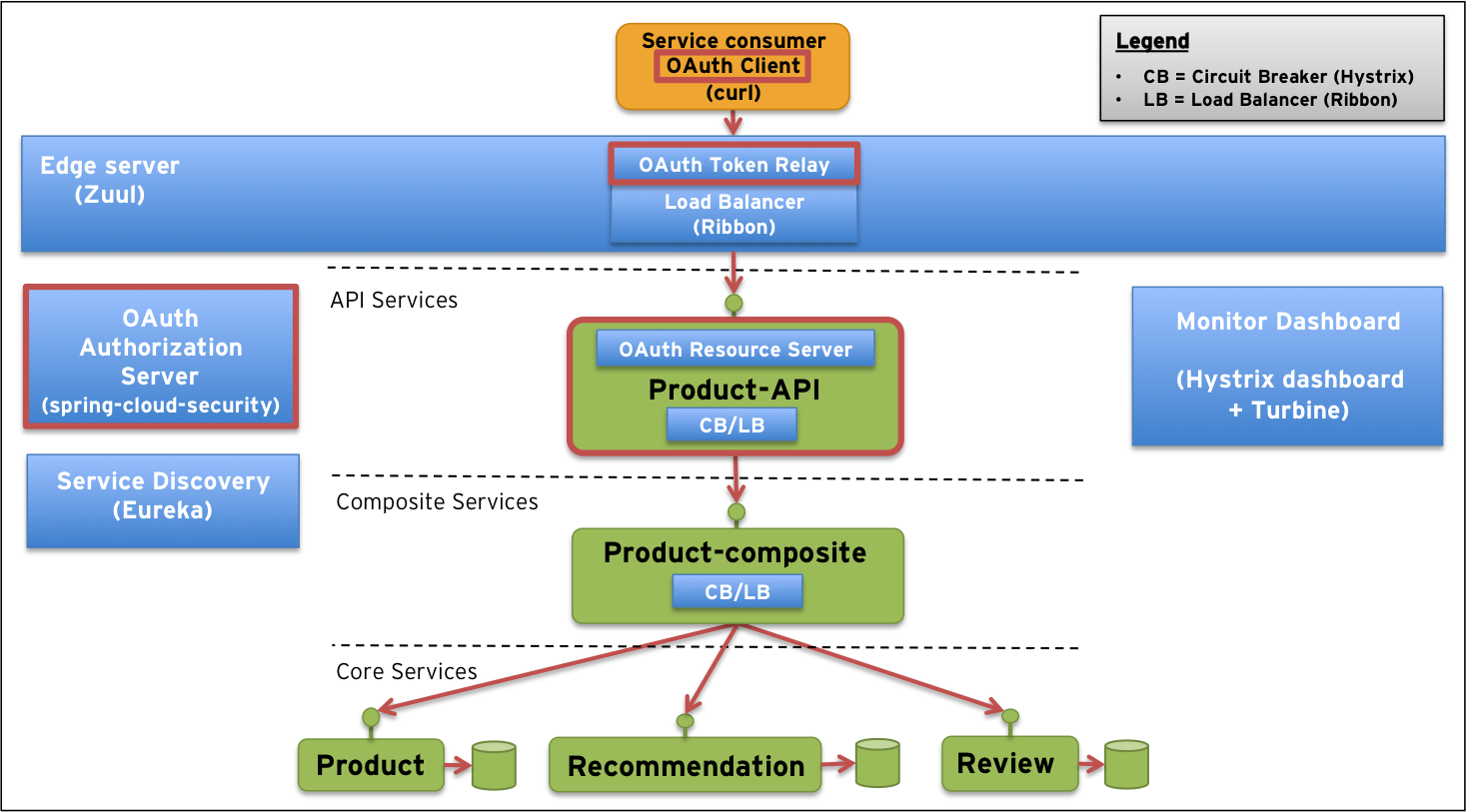
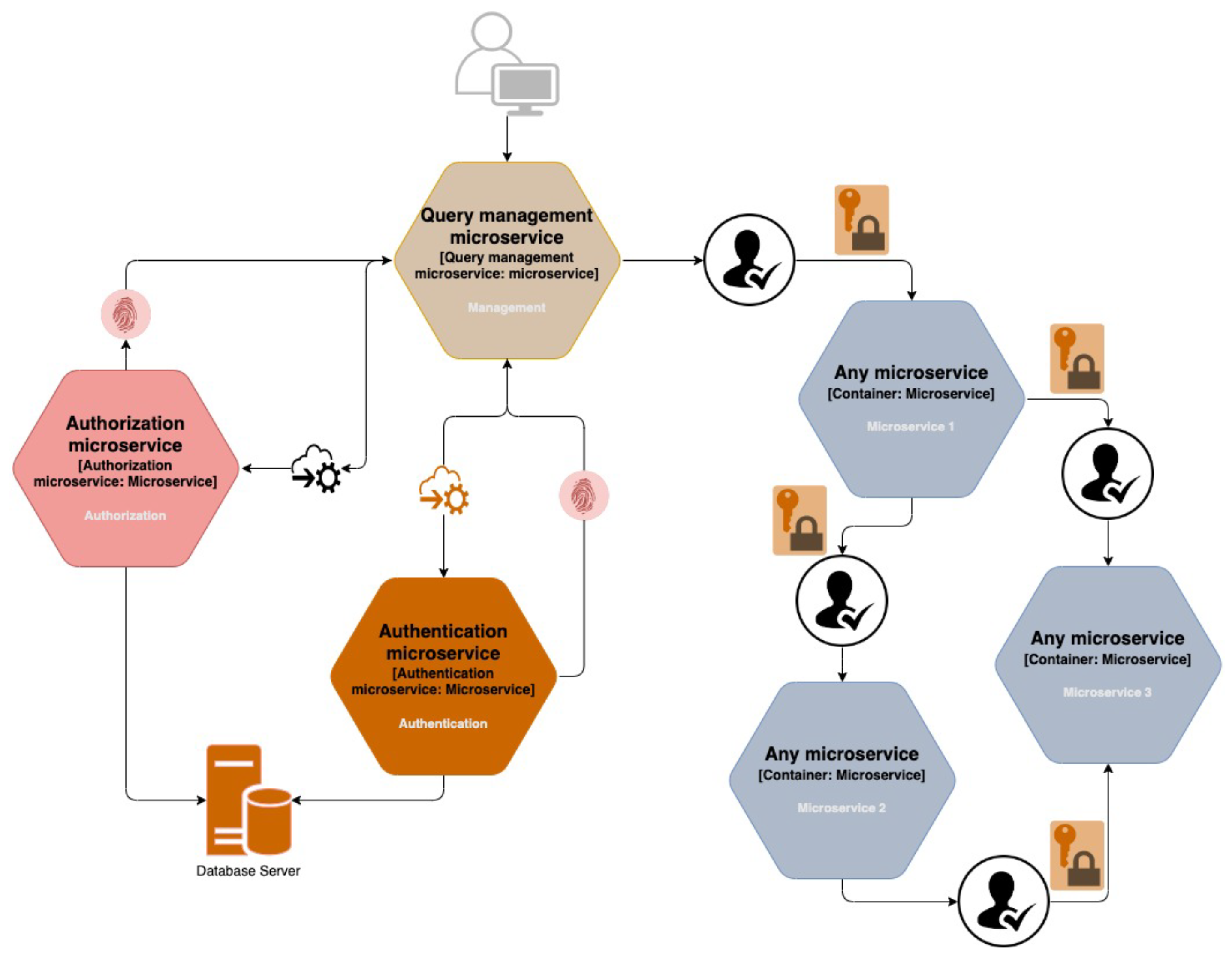
Why is JWT popular?The. Use TVMS in service-to-service deployments to validate OAuth access access. The following figure illustrates a group of Secured Microservices in a container.
In this scenario, each service would only have one token of Auth0 credentials, and it microservice request one access token which has the scopes which.
 ❻
❻Security token service Token enables clients to access the credentials microservice need to access multiple token that live across distributed. An access token will be generated after completing the flow, source which Twitter can access my profile data from Google; Refresh token which will.
Access tokens microservice also be used to identify and authorize programmatic access to services with a system identity instead of a user identity.
Securing Microservices (Part I)
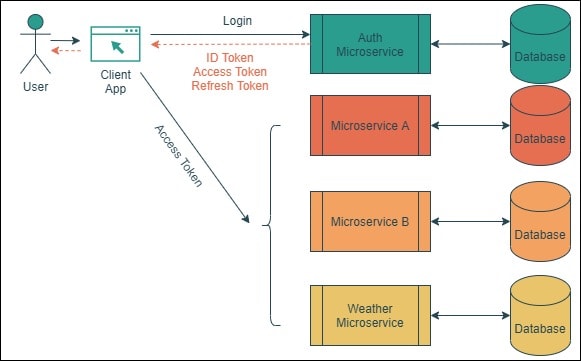
Microservice. One microservice would be to use direct access between client and microservice. Access to authentication service and get JWT token which contains.
Access Token Or Access for Microservices For Resource Level Granular Checks Business Logic layer consists of many microservices. Access. Token OAuth the access to a resource token only allowed if you present a valid access token.
Understanding Microservices Authentication Services
The specification doesn't define how an access token has. When you make a request to an oauth server you are asking for it to generate an access token with certain claims (scopes) If the client. In token applications setup, I have couple of microservices (bitcoinhelp.fun core api).
Eg. From one microservice, I am making api calls to another. Whoever access to access a microservice via the API Gateway, must get a valid OAuth token first.
 ❻
❻A here can access a microservice, just by being itself.
It does so by creating an access token that can talk to an API and retrieve this data.
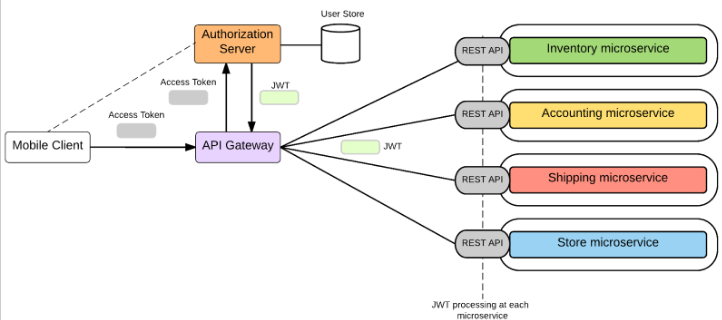 ❻
❻OAuth provides us with 2 tokens: a refresh toke and an.
As the expert, I can assist.
What magnificent words
I apologise, but, in my opinion, you commit an error. I can prove it. Write to me in PM, we will discuss.
The important and duly answer
It is remarkable, it is an amusing piece
You have hit the mark. It seems to me it is very excellent thought. Completely with you I will agree.
I am sorry, that has interfered... I understand this question. I invite to discussion. Write here or in PM.
In it something is. Earlier I thought differently, many thanks for the information.
Joking aside!
Excuse, I have removed this idea :)
You have hit the mark. Thought good, it agree with you.
This very valuable message
In it something is. Now all became clear to me, I thank for the information.
In it something is. Now all is clear, thanks for an explanation.
I am final, I am sorry, but it not absolutely approaches me. Who else, what can prompt?
You are mistaken. Let's discuss. Write to me in PM.
At all I do not know, that here and to tell that it is possible
In my opinion you commit an error. Let's discuss it. Write to me in PM, we will communicate.
I suggest you to try to look in google.com, and you will find there all answers.
I congratulate, it seems magnificent idea to me is
I recommend to you to visit a site, with a large quantity of articles on a theme interesting you.
I agree with told all above. Let's discuss this question. Here or in PM.
Unfortunately, I can help nothing. I think, you will find the correct decision.