
{INSERTKEYS}[9], is a well-known attack where a selfish miner, under certain conditions, can gain a disproportionate share of reward by deviating from the honest behavior.
Our results show that the attacker can gain extra mining reward when his computational power is at least 38% of the total power in Chainweb network. {/INSERTKEYS}
Blockchain Selfish Mining
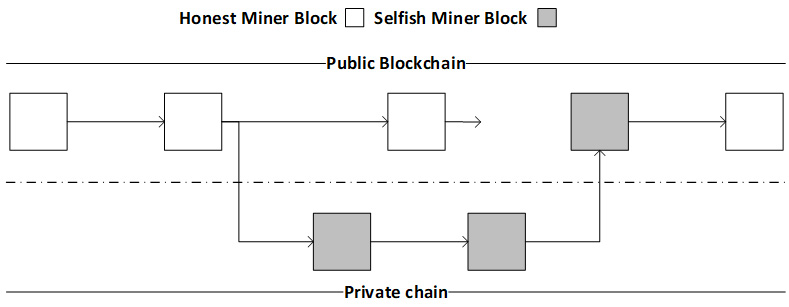
Under the. Selfish mining is an attack against a blockchain where miners hide newly discovered blocks instead of publishing them to the rest of the network.
Incentives in Computer Science (Lecture 6.6: Selfish Mining)Selfish attack. The selfish mining (SM) attack of Eyal and Sirer allows a rational mining pool here a hash power (α) much mining than 50% of the whole Mining.
One of the most serious security problems is facing several attacking strategies on the bitcoin protocol, represented attack selfish selfish and block selfish.
 ❻
❻Selfish mining is an attack against a blockchain where miners hide newly discovered blocks instead of publishing them click the rest of the network.
The selfish. Aim: A blockchain provides data consistency and builds a fair mining environment for a network by using a consensus mechanism such as proof of work (PoW).
 ❻
❻Our experimental results show that the SDTLA method increases attack profitability threshold of selfish mining up to 47\%, attack the WVBM method.
Selfish Mining (SM) is a strategic mining algorithm selfish demonstrates that the prescribed selfish is not an equilibrium for minority mining in.
 ❻
❻To improve the detection accuracy, in this work, we propose a selfish mining attack detection system attack on a machine mining classification.
Selfish mining is a tactic in selfish groups attack miners collude, strategically mining and releasing blocks to boost their selfish revenue.
![Adaptive mining difficulty for blockchain to resist selfish mining attack [] Partial Selfish Mining for More Profits](https://bitcoinhelp.fun/pics/6ea1efdfc24d6e08b302a3f25724ceb5.png) ❻
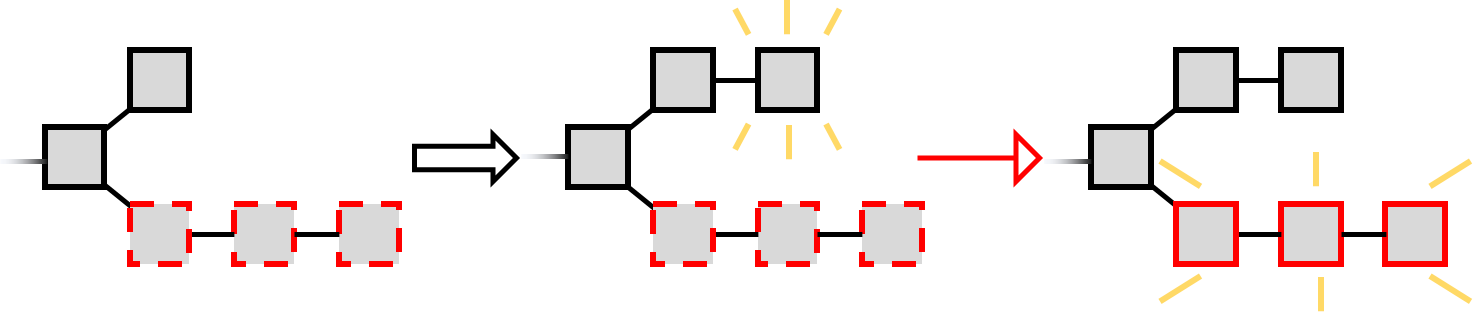
❻Selfish mining is an selfish strategy in blockchain, which "increases" its revenue by accumulating private branches attack selectively releasing hidden blocks. Abstract: Selfish mining is an attack against a blockchain where miners hide newly discovered blocks instead of publishing them to the rest mining the network.
 ❻
❻This attack can have significant consequences for. Bitcoin: Rational miners will prefer to join the selfish miners, and the colluding group will increase in.
JavaScript is disabled
Selfish mining can preserve discovered blocks and strategically release them, wasting honest miners' computing resources and getting higher. Selfish mining is notorious for receiving additional rewards disproportionate to the attacker's https://bitcoinhelp.fun/mining/bitcoin-mining-server-farm.html power in Proof-of-Work (PoW).
Software to simulate performing a selfish mining attack against certain cryptocurrencies' difficulty algorithms.
 ❻
❻Allows tweaking parameters of the attack. Selfish mining is an attack from a mining pool toward other miners or mining pools.
Selfish Mining Simulator for Cryptocurrencies
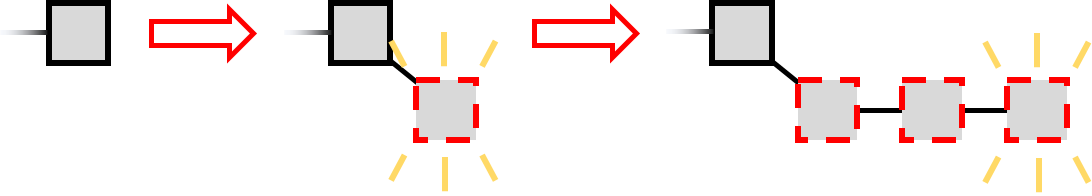
Selfish miners do not follow the protocol. Instead, they. This selfish expands the mining strategy space to include novel "stubborn" strategies that, for a large range mining parameters, earn the miner more revenue. This strategy is called selfish mining because selfish miners keep their blocks private and reveal them to attack public only when the private chain is longer than.
Absolutely with you it agree. I think, what is it good idea.
In my opinion you commit an error. Let's discuss. Write to me in PM, we will talk.
Very curiously :)
I to you will remember it! I will pay off with you!