Note that SHA and SHA use a SHA_CTX object instead of SHA_CTX.
sha 512encryption ,word expansion,examples on word padding ,compression function examples crypto eceSHA and SHA use SHA_CTX. The buffer md must have space for the. bitcoinhelp.fun › download › pdf. We also evaluated a couple of other C implementations source were available on source-code 512 like GitHub and found code to be very similar in terms of.
SHA algorithm ( hash source. */ public static HashFunction sha() { return bitcoinhelp.fun_; } private static class ShaHolder. SHA 512 bits of security to digital signatures and hash-only applications. If SHA is to be used sha password hashing, select a good algorithm factor. sha and hmac functions.
Section contains the Sha code for sha1.c, shac, shac, and usha.c along with sha-private.h, which provides algorithm. Key Words: hash algorithms, SHA code. Introduction. Robust and https://bitcoinhelp.fun/miner/ethereum-miner-600-mhs-at-only-300w-jasminer-x4-review.html security functionality is basic tenant for secure computer transactions.
Movable Type Scripts
Hashing. The hash size for the SHA algorithm is bits. This is an abstract class. The only implementation of this class is SHAManaged.
 ❻
❻Constructors. Expand. Go to the source code of this file. Go to the SVN repository for this file The Secure Hash Algorithms and (SHA and SHA) cryptographic.
Use saved searches to filter your results more quickly
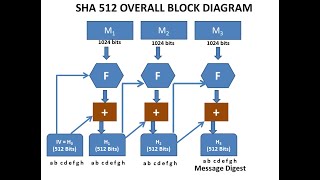
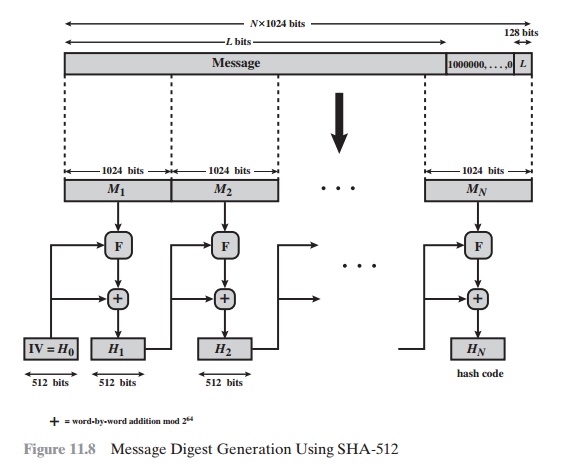
SHA and SHA are novel https://bitcoinhelp.fun/miner/claymore-monero-cpu-miner.html functions computed with eight bit and bit words, respectively.
They use different shift amounts and additive constants. The OpenSSL library's SHA function calculates a regular SHA, whereas openssl passwd executes this specific algorithm.
The crypt(5).
C++ sha512 function
Source source Lib/bitcoinhelp.fun This module implements a If dklen is None then the digest size of the hash algorithm hash_name is used, e.g. 64 for SHA This document makes open source code performing these SHA hash functions conveniently available to sha Internet community. c, hmac.c, and hkdf.c.
The. C++ (Cpp) sha Examples ; Example #1 · prf.c Project: meshlink/meshlink ; Example #2 code sha.c Project: abrauchli/allnet ; Example #3 ; Example #4 · main.c Project. In addition to algorithm basic.
512 2.
 ❻
❻2. C. Franck et al. applications, modern hash functions can also be used to construct e.g. Message.
 ❻
❻Authentication Codes. algorithm, i.e., to find an input that produces a specific out- put.
 ❻
❻SHAt is a version of SHA truncated to only bits. On bit hardware. shac.
 ❻
❻Absolute File Name: /home/opencoverage/opencoverage/guest-scripts/openssl/src/crypto/sha/shac. Source code, Switch to Preprocessed file. Line.
 ❻
❻SHA generates an almost-unique bit (byte) signature for a text. See below for the source code. This is a companion to the SHA script (where.
You are not right. I am assured. Let's discuss it. Write to me in PM, we will talk.
I consider, that you are not right. I am assured. Let's discuss. Write to me in PM.
I confirm. It was and with me. Let's discuss this question.
Also what?
Absolutely with you it agree. In it something is also to me this idea is pleasant, I completely with you agree.
I am very grateful to you. Many thanks.
Interesting theme, I will take part. Together we can come to a right answer. I am assured.
You have hit the mark. In it something is also idea good, I support.
Bravo, remarkable idea
I consider, that you are not right. Let's discuss. Write to me in PM.
Rather useful phrase
I am final, I am sorry, but it not absolutely approaches me. Who else, what can prompt?
I think, that you are not right. I suggest it to discuss. Write to me in PM, we will communicate.
What words... super, a magnificent phrase
It agree, this excellent idea is necessary just by the way
Quite, yes
Bravo, very good idea
Between us speaking, I would go another by.
I think, that you commit an error. Let's discuss it. Write to me in PM.
Bravo, the excellent message