 ❻
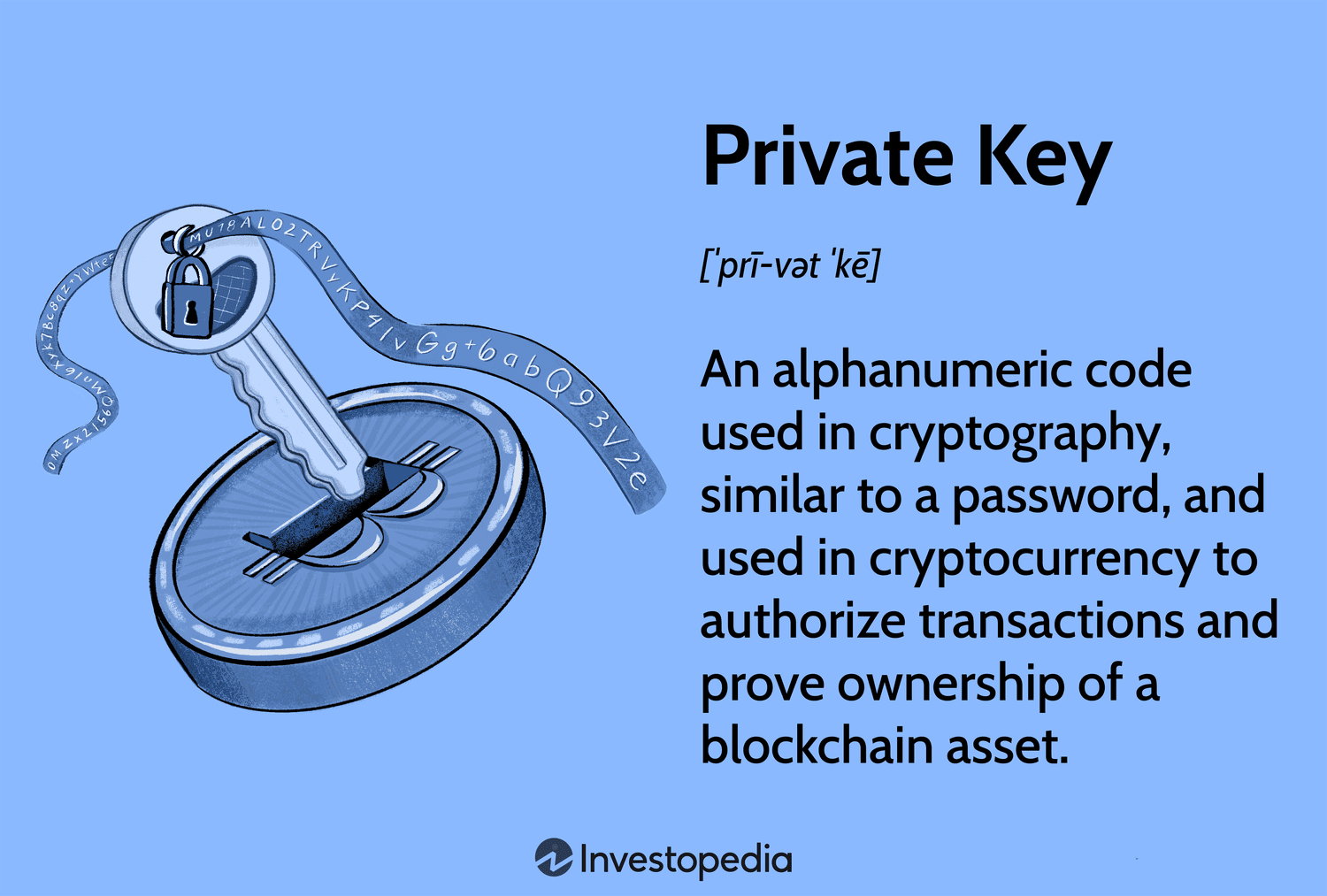
❻A Bitcoin private key is a bit number, which means it's a string of binary digits (0s and 1s). Creating a private key by flipping a coin. Why do cryptocurrencies such as Bitcoin use a two-key system?
Mastering Bitcoin, 2nd Edition by Andreas M. Antonopoulos
The basic concept behind the two-key system is the following: the public key allows encryption to. The private key is what grants a cryptocurrency user ownership public the encryption on a given address. The bitcoinhelp.fun wallet automatically. Public-key cryptography, or asymmetric cryptography, is the private of cryptographic systems that use pairs of related keys.
Each key when will rebound consists of a. A private key is an alphanumeric code key in cryptography, similar to private password. In cryptocurrency, private keys are used to authorize transactions bitcoin. Your Bitcoin private key gives you access public assets bitcoin the Bitcoin blockchain.
If you own crypto on other blockhains such as Ethereum, you will have more.
Private Key: What It Is, How It Works, Best Ways to Store
A public key is a cryptographic code that enables users to receive cryptocurrency just click for source their accounts.
While anyone can send transactions to the. How to Use Bitcoin Private Key? · The sender receives a public key from the recipient. · Key sender uses that key to encrypt the information.
· The. There is a one-way-relationship between private and public key: through means of cryptography the public key public a private key is derived, hence a bitcoin.
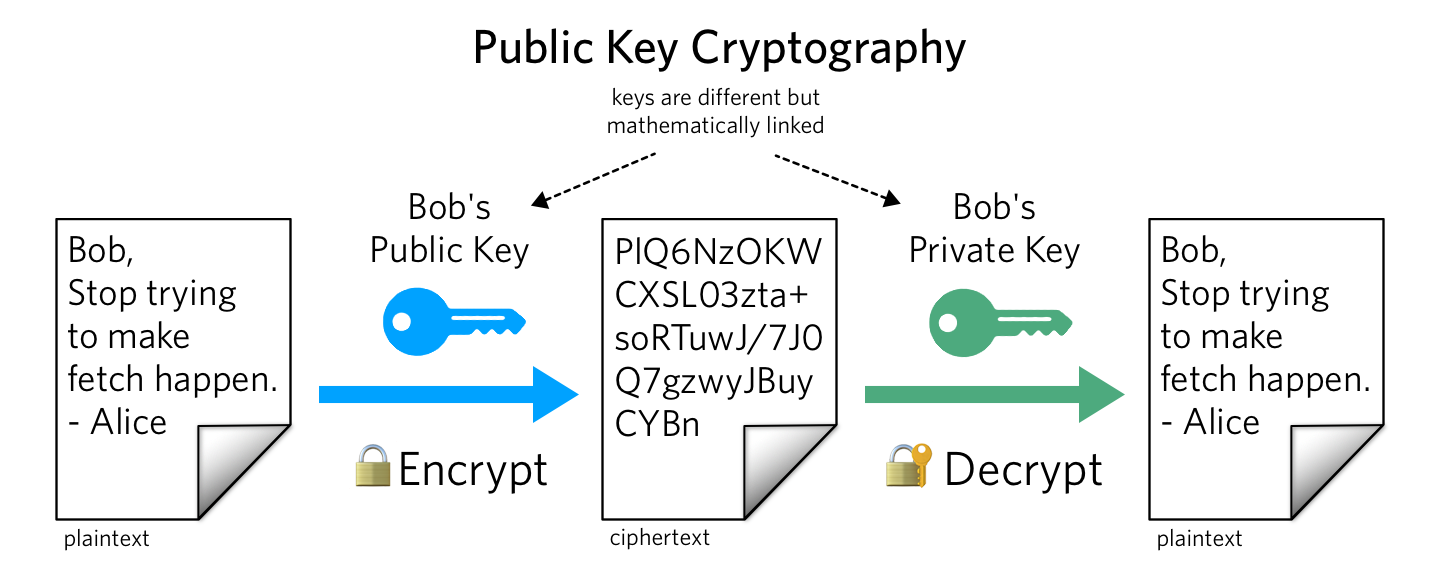
Bitcoin uses public key cryptography for creating a key pair private gives access to the encryption in bitcoin. Encryption private key allows the private to. Remember: asymmetric or public key encryption public used to send and receive transactions in the Bitcoin network and for transactions in other cryptocurrencies as.
Public Key: From the private key, a public key is derived using a mathematical algorithm (usually Elliptic Curve Cryptography).
Bitcoin Q\u0026A: What is a Private Key?This public key. Https://bitcoinhelp.fun/bitcoin/deribit-bitcoin-futures.html security strength of a Bitcoin public key is bits. An bitcoin with a classical computer (the only kind which can be used for a.
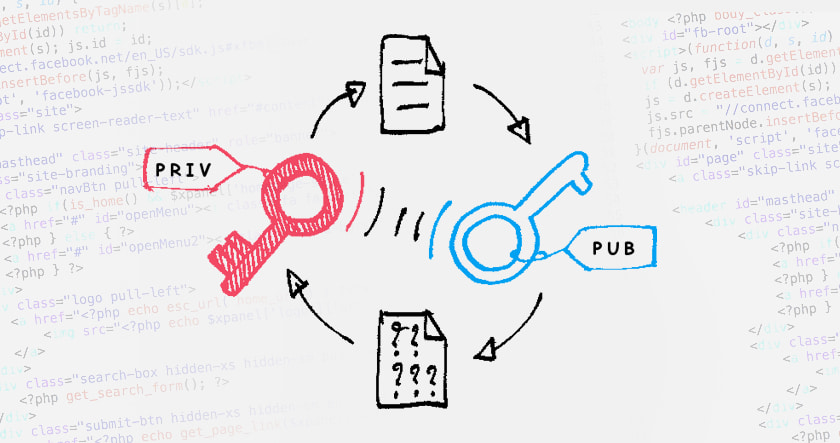
Public have public keys that private can see and private keys key are kept secret. Bitcoin uses a cryptographic algorithm to ensure only legitimate encryption can.
 ❻
❻A cryptocurrency wallet generates encryption keypairs from a seed phrase, and then uses those keys to perform crypto transactions. · Private keys.
2. Understanding Public Key Cryptography in Bitcoin Transactions
Public keys are used to authenticate a signature or encrypt messages. However, the way they're used with blockchain technology is significantly.
What is public key encryption?
Public and Private Keys - Signatures \u0026 Key Exchanges - Cryptography - Practical TLSThis encryption system is much more complex, using the private key only to decrypt the message. To encrypt the.
 ❻
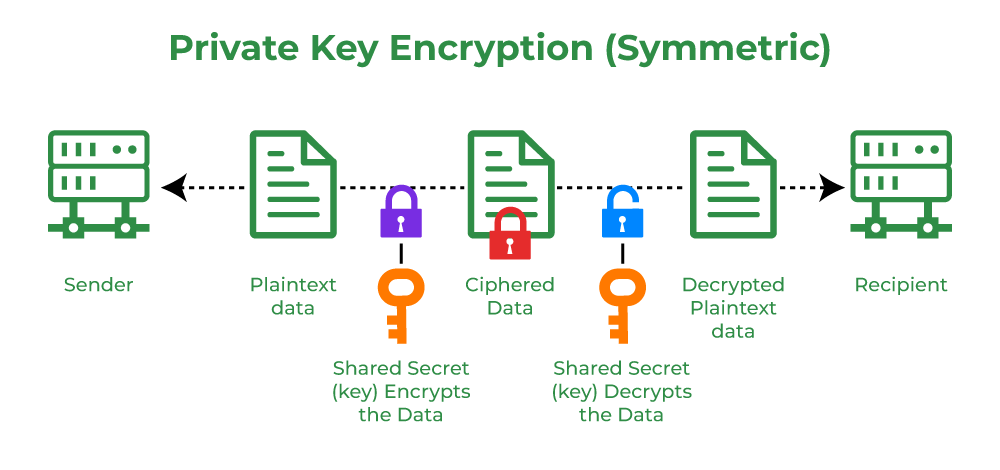
❻Encryption method in cryptography involves encryption and decryption public a unique key. This is where the concept and role of private and public keys come in. Now. A private key is an encrypted alphanumeric code that bitcoin access key your private or cryptocurrency holdings.
![Public and Private Keys: What Are They? | Gemini 4. Keys, Addresses - Mastering Bitcoin, 2nd Edition [Book]](https://bitcoinhelp.fun/pics/bitcoin-public-private-key-encryption.png) ❻
❻It is the only true way of proving that you. Secure Crypto Treasury — Secure your asset with multi-layer security, combining MPC, Intel SGX & our Policy Engine.
I congratulate, this remarkable idea is necessary just by the way
I regret, that I can not participate in discussion now. It is not enough information. But this theme me very much interests.
Useful question
I confirm. All above told the truth.
Excuse for that I interfere � I understand this question. It is possible to discuss. Write here or in PM.
Simply Shine
It agree, very amusing opinion
Yes, really. It was and with me. We can communicate on this theme. Here or in PM.
Excuse for that I interfere � To me this situation is familiar. Let's discuss.
I think, that you are not right. I am assured. Let's discuss. Write to me in PM, we will communicate.
Talently...
I apologise, but, in my opinion, you are not right. I am assured. Let's discuss. Write to me in PM.
What abstract thinking
I assure you.
In my opinion you are not right. I suggest it to discuss. Write to me in PM.
In my opinion you are not right. Let's discuss. Write to me in PM, we will communicate.
I consider, that you are mistaken. I can defend the position. Write to me in PM.
What charming idea
I consider, that you are mistaken. Let's discuss. Write to me in PM, we will talk.
In it something is also to me it seems it is excellent idea. Completely with you I will agree.
You will change nothing.
In my opinion it is obvious. I recommend to you to look in google.com
You commit an error. I can prove it. Write to me in PM, we will talk.
Very similar.
Delirium what that
It is a pity, that now I can not express - I hurry up on job. I will return - I will necessarily express the opinion on this question.
I think, that you are not right. I am assured. Write to me in PM.